A ‘brute force’ login attack is a type of attack against a website to gain access to the site by guessing the username and password, over and over again. Other kinds of hacks rely on website vulnerabilities whereas a brute force attack is a simple hit and miss method and can be tried on any site.
In this tutorial, we will cover some methods and plugins we can use to prevent brute force attacks against WordPress sites. WordPress is the most popular CMS and therefore it’s a frequent target of these type of attacks.
What’s the Difference Between a Brute Force Attack and a DDoS Attack?
A brute force attack is performed to gain access to someone else’s account on the site, whereas a DDoS attack is usually launched to take a site down (typically by consuming resources). That said, a large scale brute force attack can also take a site down.
A DDoS attack is usually performed using a bot, whereas a brute force attack can be made using a bot or by a human. Humans can launch more targeted attacks, especially if they know usernames or have other intelligence to narrow down possible credentials.
Neither of these kinds of attacks rely on the website vulnerabilities and can be applied to any website.
WordPress doesn’t have any built in feature to prevent these two types of attacks. Therefore, it’s your responsibility to prevent them on your own sites.
This tutorial will show you how you can prevent brute force attacks.
How is a Brute Force Attack Launched Against a WordPress Site?
Launching a brute force attack on a site is relatively easier than any other kinds of attack. To launch a brute force attack on a site that logs into a user account, you just need to send the login form POST requests with the guessed username and password.
In case of WordPress, the POST request with the guessed username and password is made to wp-login.php file again and again.
Let’s see some of the ways to prevent brute force attacks.
Verifying You Are Human
Most of the time, brute force attacks are made using bots. We can simply verify if a form has been submitted by a human or not. If it’s submitted by a bot then we simply don’t process it.
No CAPTCHA reCAPTCHA is a simple and user friendly way of asking the site visitor to verify if they are human or not when submitting a form.
Here are the following problems using this method:
- WordPress processes the request anyway, therefore if the brute force attack is made on large scale by bots then resources are still consumed that can kill the site.
- This method prevents access to bots but not humans.
Password Protecting wp-login.php
You can protect access to your wp-login.php file using HTTP Basic Authentication. This simply adds a extra security layer. Although a brute force attack can be launched against HTTP basic authentication but it’s difficult and time intensive to crack down both layers.
To password protect access to the wp-login.php file in Apache, follow the below steps:
- Generate a
.htpasswdfile using htpasswd generator. - Place this file in the same location as your
.htaccessfile. - Assuming your
.htpasswdfile includes the usernamenarayanprusty, place the code below in your.htaccessfile
## Stop Apache from serving .htpasswd files <Files ~ "^\.ht"> Order allow,deny Deny from all </Files> <Files wp-login.php> AuthUserFile ~/.htpasswd AuthName "Private access" AuthType Basic require user narayanprusty </Files>
Here are the following problems using this method:
- If your WordPress site has multiple authors then you may not want to share the username and password of basic authentication.
- It’s possible that a bot or human can successfully guess both passwords.
- Although WordPress is not loaded during basic authentication, a web server initiates a process to verify the credentials therefore consuming memory and CPU which can kill a site if requests are made in large scale.
Brute Force Login Protection Plugin
Brute Force Login Protection is a WordPress plugin which protects brute force login attempts by taking several factors into account.
This is how the plugin works:
- Limits the number of allowed login attempts for an IP Address.
- It allows you to manually block an IP address from logging into WordPress
- It delays execution after a failed login attempt to slow down the brute force attack. This can prevent the site being killed.
- It also informs the users about the number of login attempts remaining before getting blocked.
This is how the settings page of the plugin looks:
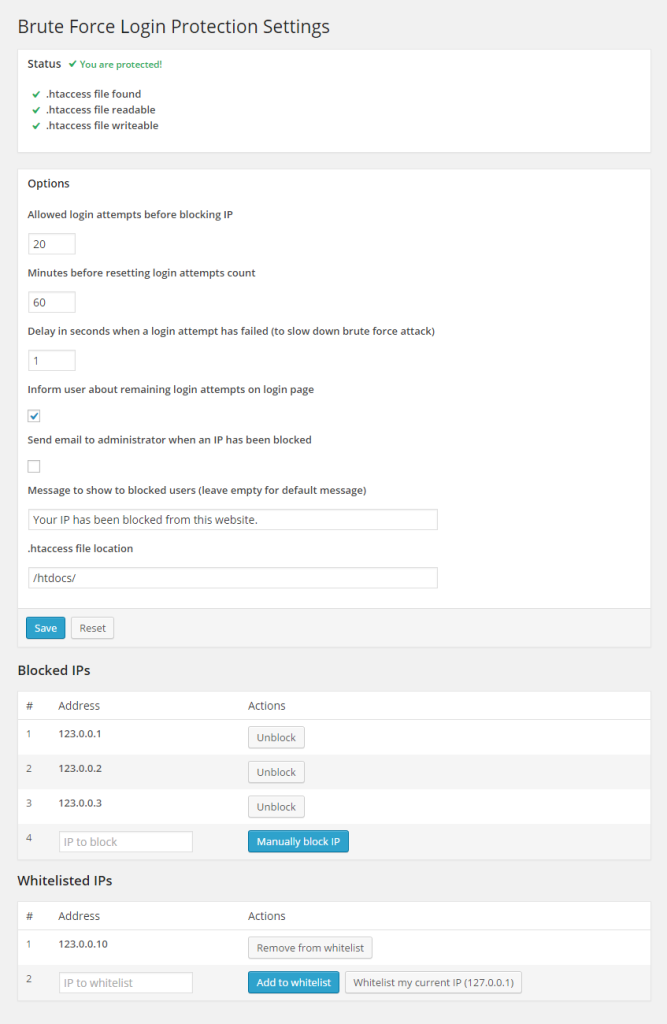
Here are the following problems using this plugin:
- It will not be able to deal well with a distributed brute force attack because this plugin completely relays on IP address. A distributed brute force attack is one made from many different computers i.e. different IP addresses.
- It delays script execution for an IP address if a login has failed previously. While this saves computational time, memory is still used as the process is created in memory.
BruteProtect
BruteProtect is a cloud-powered Brute Force attack prevention plugin and aims to provide the best protection against botnet attacks.
Every WordPress site which has BruteProtect installed will become a part of BruteProtect network. When an IP address is blocked due to malicious activity (such as a some number of failed login attempts) it’s shared among all the sites so that they all can block it before it begins to harm any sites.
You can think of BruteProtect as an advanced version of the above Brute Force Login Protection plugin as it has a bigger list of bad bots therefore probably doing well in the case of a distributed brute force attack.
One feature that the BruteProtect plugin doesn’t have that the Brute Force Login Protection plugin does is a slow down script execution for failed login attempts. However, it doesn’t matter that much, as it takes up memory for the extra time.
The problem using this plugin is that WordPress is loaded on every request for the IP address verification to be done. Therefore, if a brute force attack is done on a large enough scale then the site can still become overwhelmed and fall over.
CloudFlare
CloudFlare protects and accelerates any website online. Once your website is a part of CloudFlare, its web traffic is routed through their intelligent global network. They automatically optimize the delivery of your web pages so your visitors get the fastest page load times and best performance.
What’s important is it can prevent brute force attacks. Its has free and premium plans. Free plan is enough to get a decent amount of brute force protection. All the methods we’ve seen above were making our web server do the work to prevent brute force attack, which as we’ve mentioned, can still consumes memory and CPU. But CloudFlare on the other hand, can prevent malicious requests, before they even hit your server.
This image below shows how CloudFlare stops malicious requests:
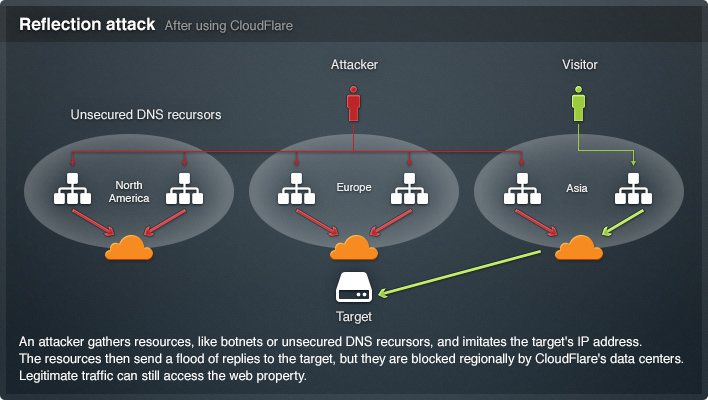
Here are the following problems using this service:
1. You need to make DNS changes to integrate CloudFlare with your site. This can be difficult if you’re not overly technical.
2. It fails to stop brute force attacks made by humans. It’s good at identifying malicious bots, but not malicious humans.
Conclusion
You must be wondering which is the best solution? It really depends on which one you think is the best for your needs. For me personally, I use both CloudFlare and BruteProtect to stops brute force attacks on my site.

